How to Meet FedRAMP's Requirements for Container Vulnerability Scanning
The federal government continues to work to increase cybersecurity efforts in the United States, including, of course, in cloud environments. Specifically focused on cloud products and services, FedRAMP (the Federal Risk and Authorization Management Program) provides a standardized approach to security assessments, authorization, and continuous monitoring. The vulnerability scanning requirements for containers in FedRAMP bridges compliance gaps between traditional cloud systems and containerized cloud systems.
Rapid changes in technology require continuous monitoring for cloud service providers (CSPs) to maintain the security of FedRAMP authorized systems. The adoption of microservices, containers, and Kubernetes continues to grow as organizations adopt cloud native deployments. While this guidance is obviously helpful for FedRAMP certification, they are also best practices for any organization looking to secure their use of containers and Kubernetes. With the increased adoption and deployment of Kubernetes and containers, it’s more important than ever to scan containers for vulnerabilities, from development through to deployment. FedRAMP outlines clear requirements for this, including:
-
Hardened Images: The Cloud Service Provider (CSP) must use only containers where the image is “hardened.” The hardening must be in accordance with relevant benchmarks listed in the National Checklist Program and defined by the National Institute of Standards and Technology (NIST) SP 800-70 (where applicable).
-
Container Build, Test, and Orchestration Pipeline: The CSP must use automated container orchestration tools to build, test, and deploy containers to production. Any automated container orchestration tools must be validated by a Third Party Assessment Organization (3PAO) to meet the baseline controls CA-2, CM-2, CM-3, SC-28, SI-3, and SI-7.
-
Vulnerability Scanning for Container Images: Before deploying containers to production, a CSP must make certain that all components of the container image are scanned based on the requirements outlined in FedRAMP Vulnerability Scanning Requirements. Scanning should be one of the steps in the deployment pipeline (where possible). The 30-day scanning window begins when the container is deployed to the production registry and only those that have been scanned within that 30-day window may be actively deployed in the production environment.
-
Security Sensors: Deployment of independent security sensors alongside production-deployed containers can help to continuously inventory and assess a CSP’s security posture. Security sensors must run with sufficient privileges to avoid lack of visibility and false negatives. Deploy these sensors everywhere containers execute, including within registries, as general-purpose sensors, and within CI/CD pipelines.
-
Registry Monitoring: Monitor the container registry for each unique image to ensure that containers that correspond to an image that has not been scanned within the 30-day vulnerability scanning window are not actively deployed on production.
-
Asset Management and Inventory Reporting for Deployed Containers: Assign a unique asset identifier to every class of image that corresponds to one or more production-deployed containers. Document these image-based asset identifiers in the FedRAMP Integrated Inventory Workbook Template. The CSP must track production-deployed containers using an automated mechanism that has been validated by a 3PAO to meet the baseline control CM-8.
Fairwinds Insights can help you meet many of those important container vulnerability scanning requirements. Reference the FedRAMP guidelines for additional details on the scanning requirements for systems using container technology.
Configure Insights to meet vulnerability scanning for container images requirements
Fairwinds Insights supports image scanning, sometimes called container scanning, to identify security vulnerabilities. It’s best practice to scan components as you build your container by integrating image scanning into the continuous integration/continuous deployment (CI/CD) process. Shifting scanning left, earlier into the development process, allows you to detect and block vulnerabilities before the code enters the pipeline.
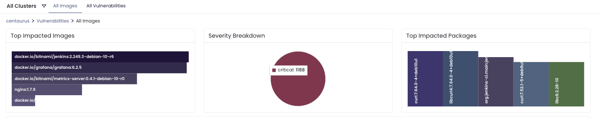
It’s also important to scan for open source vulnerabilities in your images at runtime. Insights provides continuous, automated scanning to identify new Common Vulnerabilities and Exposures (CVEs) as soon as they are publicly disclosed. Your environment may contain many applications and Kubernetes clusters, so it is important to have visibility into any container vulnerabilities across all environments and from development through deployment.
Your container registry contains hundreds or thousands of container images built from different sources, including third parties. Keeping track of updates to third-party add ons and container images can be difficult for many teams, which is why Insights recommends upgrade paths for third-party images. It does this by analyzing the image repository, identifying new tags available for a container image, and recommending a version to upgrade to that has fewer vulnerabilities than the version currently running in the cluster.
Insights also supports Kubernetes configuration scanning to identify security misconfigurations. This scanning can help you ensure that your deployed workloads and pods are compliant with Kubernetes best practices for security configurations. Fairwinds Insights also provides automated fix pull requests, which allows you to automatically fix many common Kubernetes misconfigurations. Automatically fixing these misconfigurations can help you reduce the cost of meeting FedRAMP requirements.
Infrastructure as code (IaC) enables you to define the Kubernetes cluster itself and the applications that run on the cluster, which makes it easier to manage and ensure consistency across different environments. Insights supports Terraform scanning, checking Terraform files for configuration issues that may put workloads and cloud infrastructure at risk. Integrating this scanning at the pull request stage provides your teams with an immediate feedback loop to fix issues quickly. You can also leverage policy enforcement to gate pipelines or mere requests based on IaC scan results.
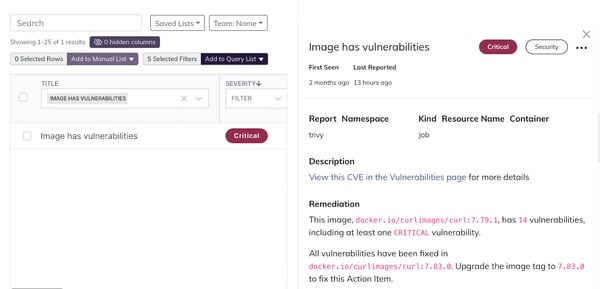
Configure Insights to meet security sensors for container images requirements
Falco is an open source project that provides runtime security, delivering real-time visibility into configuration changes, intrusions, data theft, and unexpected behaviors. Insights integrates security events from Falco, as well as new image vulnerabilities from running containers, to provide a single pane of glass to DevSecOps teams. It also enables incidents to be routed automatically to third-party tools, such as Slack and PagerDuty, to notify the appropriate team of any issues.
Configure Insights to meet registry monitoring requirements
Open Policy Agent (OPA) is another open source tool integrated into Insights, offering policy-based controls for cloud native environments. OPA is a framework for validating structured data, which you can use to enforce a known, trusted allow-list of image registries. This ensures that you are not only monitoring your deployments continuously, but also ensuring that no images can enter your environment that are not from a trusted source.
Configure Insights to meet asset management and inventory reporting for deployed containers requirements
Fairwinds Insights enables you to manage and maintain an asset inventory because it collects data about all container images across all clusters to provide a comprehensive list of every image and image version currently deployed in a Kubernetes environment. It also inventories Kubernetes workloads, including pods, services, and ingresses to provide an inventory of the assets in a cluster and identify when they are not compliant with your organization’s security policies. Role-based access control (RBAC) profiles help you create unique roles for the infrastructure team, developers, users, service accounts, and administrators. Insights provides an inventory of RBAC profiles, which makes authorization simpler to manage.
Meet FedRAMP Container Vulnerability Scanning Requirements
Meeting the requirements for FedRAMP certification will help you secure your use of containers and Kubernetes. Shifting to cloud native technologies and deploying more applications and services to production environments in Kubernetes highlights the importance of maintaining the security of containers.
If you want to see how Insights can help you meet FedRAMP container vulnerabilities scanning requirements but you are not currently a Fairwinds Insights customer, try our free tier for environments up to 20 nodes, two clusters, and one repo. (Not sure how to get started? This post that walks you through the simple process.) If you are already a Fairwinds Insights user, log in to the user interface (UI) and configure Insights as described above. With these changes, you can meet these FedRAMP requirements for container vulnerability scanning.


